(Plesk for Windows) Tune Plesk to Meet PCI DSS¶
In this topic, you will learn how to secure your server and achieve compliance with PCI DSS on a Microsoft Windows-based server.
Warning
We highly recommend that you configure the Windows firewall in the server operating system to block all remote procedure calls (RPC) and communications to the Windows Management Instrumentation (WMI) services.
Disabling insecure SSL/TLS ciphers and protocols¶
SSL/TLS ciphers and protocols version 1.0 and 1.1 contain vulnerabilities and pose a security risk. PCI DSS recommend disabling them and using TLS 1.2 or later. Learn how to disable insecure ciphers and protocols.
Securing Remote Desktop connections¶
To prevent man-in-the-middle attacks, set up encryption of the remote desktop connections.
Changing Remote Desktop connections port¶
Some PCI scanners report a man-in-the-middle attack if you do not change the RDP port to a custom value. To do it, complete the following steps:
Run the
regeditutility by clicking Start > Run, typing regedit, and then clicking OK.Change the port value by modifying the following registry key:
HKEY_LOCAL_MACHINESystemCurrentControlSetControlTerminalServerWinStationsRDP-TcpPortNumber
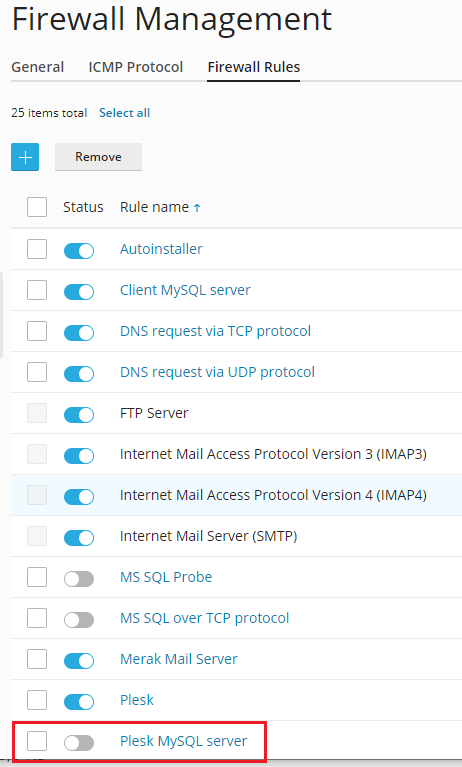
Prohibiting access to MySQL/MariaDB database server from external addresses¶
Use the firewall functions built into your Plesk.
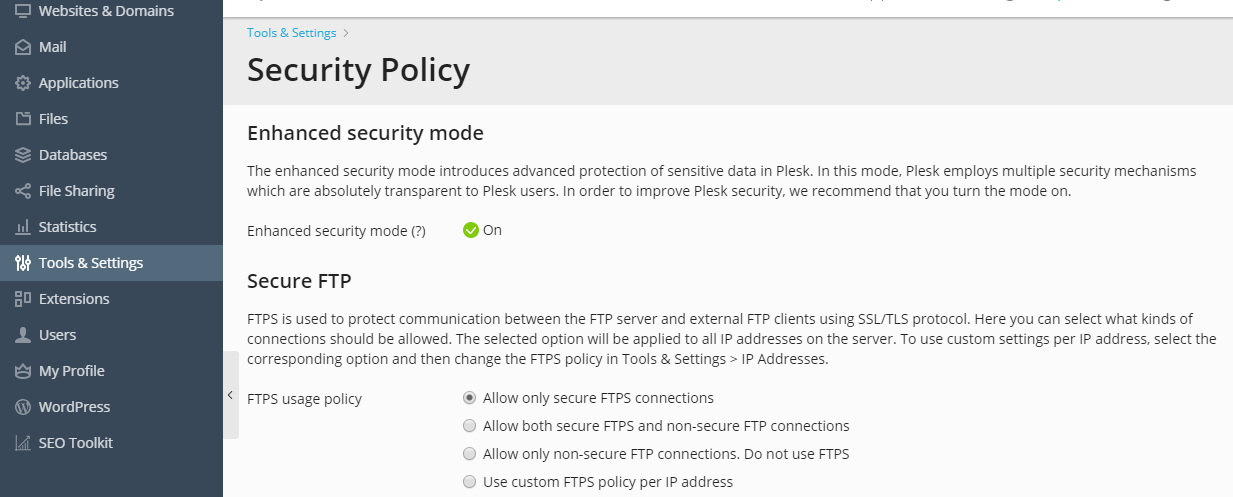
Securing FTP connections¶
If you allow FTP connections to your server, you must prohibit all FTP connections except secure FTPS connections.
To allow only FTPS connections to your server: