(Plesk for Linux) Tune Plesk to Meet PCI DSS¶
This section describes the steps that you should take if you want to secure your server and achieve compliance with PCI DSS on a Linux server.
Installing the latest version of software¶
Before you begin, it is recommended to update all the software on your server to the latest versions, if it is possible.
Disabling weak SSL/TLS ciphers and protocols¶
Next, you need to run the PCI Compliance Resolver utility available from the Plesk installation directory. This will disable weak SSL/TLS ciphers and protocols for web and e-mail servers operated by Plesk, and will also make other security changes.
To run the utility:
Log in to the server shell.
Issue the following command:
plesk sbin pci_compliance_resolver {--enable|--disable} [<service>]
The following values may be used for the <service> argument:
panel- Applying security changes for sw-cp-server (nginx for Plesk).apache- Applying security changes for Apache server.courier- Applying security changes for Courier IMAP.dovecot- Applying security changes for Dovecot.qmail- Applying security changes for qmail.postfix- Applying security changes for Postfix MTA.proftpd- Applying security changes for ProFTPd.all- Applying security changes for all installed services described above. This is a default value.
Running the utility with the --enable option applies the following
security changes to the specified services:
- Sets the following list of ciphers:
"EECDH+AESGCM+AES128:EECDH+AESGCM+AES256:EDH+AESGCM+AES128:EDH+AESGCM+AES256:EECDH+SHA256+AES128:EECDH+SHA384+AES256:EDH+SHA256+AES128:EDH+SHA256+AES256:EECDH+SHA1+AES128:EECDH+SHA1+AES256:EDH+SHA1+AES128:EDH+SHA1+AES256:EECDH+HIGH:EDH+HIGH:AESGCM+AES128:AESGCM+AES256:SHA256+AES128:SHA256+AES256:SHA1+AES128:SHA1+AES256:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!KRB5:!aECDH:!EDH+3DES". - On the latest versions of operating systems, sets the following
protocols:
"TLSv1.1 TLSv1.2". On the older versions (including CentOS 5, Red Hat Enterprise Linux 5, CloudLinux 5), sets the following protocols:"TLSv1 TLSv1.1 TLSv1.2"(actually, onlyTLSv1will work on those operating systems). - Sets the DH parameter’s size to 2048.
- Disables SSL/TLS compression.
- Sets
disable_plaintext_auth = yesfor Dovecot. - Disallows plaintext authentication for non-encrypted connections for Courier.
Running the utility with the --disable option partly reverts the
changes made by the utility with the --enable option. In
particular, the DH parameter size and SSL/TLS compression settings
remain as it is, while the list of ciphers and protocols are reverted to
the default set (this set contains the "TLSv1 TLSv1.1 TLSv1.2"
protocols and the "HIGH:!aNULL:!MD5" ciphers).
If you need to change protocols and/or ciphers for all services, you can
call the server_pref utility (the details of using this utility can
be found in server_pref: Interface and System Preferences).
If you need to set specific parameters for some services, call manually the sslmng utility:
plesk sbin sslmng --ciphers="EECDH+AESGCM+AES128:EECDH+AESGCM+AES256:EDH+AESGCM+AES128:EDH+AESGCM+AES256:EECDH+SHA256+AES128:EECDH+SHA384+AES256:EDH+SHA256+AES128:EDH+SHA256+AES256:EECDH+SHA1+AES128:EECDH+SHA1+AES256:EDH+SHA1+AES128:EDH+SHA1+AES256:EECDH+HIGH:EDH+HIGH:AESGCM+AES128:AESGCM+AES256:SHA256+AES128:SHA256+AES256:SHA1+AES128:SHA1+AES256:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!KRB5:!aECDH:!EDH+3DES" --protocols="TLSv1.1 TLSv1.2" --strong-dh --disable-tls-compression
Add the option "--service <some_service>" to the command above and
change the SSL/TLS settings of a particular service if necessary.
Note
The changes made by the sslmng utility can be overwritten by the
subsequent call of the server_pref utility or by a Plesk update.
Limitations¶
The following limitations exist:
- The protocols for qmail mail agent cannot be configured; therefore, qmail is not secure enough to satisfy PCI DSS. It is recommended to use Postfix instead.
- Ciphers for qmail cannot be changed via Plesk utilities (though it is possible to change them via the configuration file).
- TLSv1.1 and TLSv1.2 are not supported on CentOS 5, Red Hat Enterprise Linux 5, and CloudLinux 5.
- The DH parameter’s size cannot be managed for Apache from OS vendor (CentOS 5, Red Hat Enterprise Linux 5, CloudLinux 5).
- SSL/TLS compression is not disabled on Debian 7 for ProFTPd, Dovecot, and Postfix.
Prohibiting external access to the MySQL/MariaDB database server¶
You also need to prohibit access to the MySQL/MariaDB database server from external addresses. To do this, run the following command:
plesk sbin mysqlmng --bind-address local
Protecting information about files¶
To alleviate security risks arising from disclosure of information about files and their properties by Apache Web server, add the FileETag directive in the Web server configuration file.
To do this:
- Open for editing the Web server’s configuration file:
- On Debian and Ubuntu, it is located
at
/etc/apache2/plesk.conf.d/roundcube.htaccess.inc. - On other distributions of Linux, it is located
at
/etc/httpd/conf/httpd.conf.
- On Debian and Ubuntu, it is located
at
- Add the line
FileETag MTime Sizeand save the file. - Restart the Web server.
On Debian package-based systems, issue the
command /etc/init.d/apache2 restart.
On RPM package-based systems, issue the
command /etc/init.d/httpd restart.
Securing FTP access¶
To prevent ProFTPd from showing information about its version on FTP connections:
- Open for editing the ProFTPd configuration
file
/etc/proftpd.conf. - Insert the following line into the file:
ServerIdent off. - Save the file.
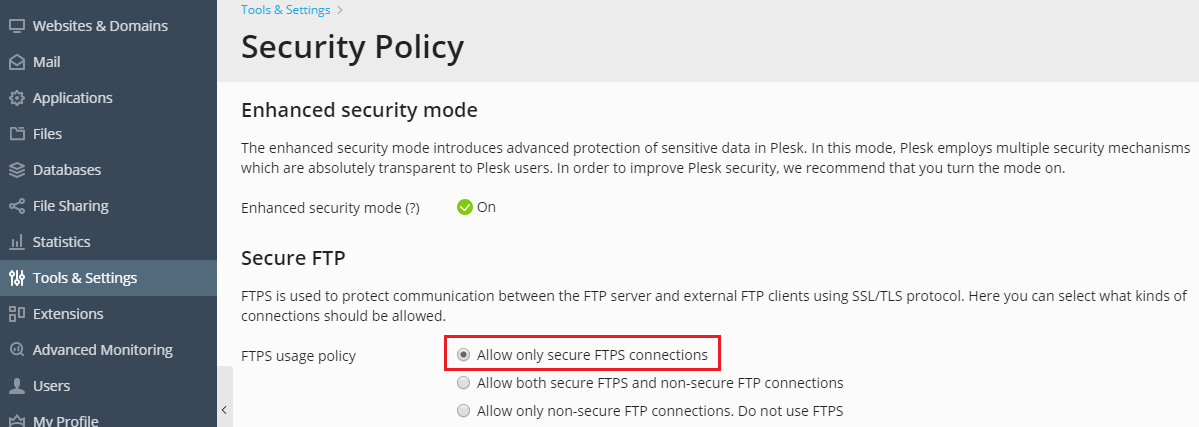
If you allow FTP connections to your server, you must prohibit all FTP connections except secure FTPS connections.
To allow only FTPS connections to your server: